































Accelerate Threat Hunts and Investigations with Pre-Curated Complex Queries
Security teams often lack the ability to gain deep visibility into the state of all their endpoints in real time. Even with a bevy of tools at their fingertips, once an incident occurs, conducting investigations can be likened to searching for a needle in a haystack. Teams struggle to make well informed remediation decisions fast enough, finding themselves asking questions like, what should I be searching for? Where specifically in my environment should I zero-in? Which datasets matter? Which are irrelevant?The struggle is real.As we all know, the longer a threat runs wild, the more havoc it stands to wreak on your environment. Between the intense time-pressure, endless datasets to sift through, and ambiguity associated with not knowing where or how to start, incident investigations can feel like frenzied wild goose chases.
Many teams have adopted threat hunting to take a more proactive and preventative (rather than purely reactive) approach to managing their security hygiene. With 43% of organizations performing continuous threat hunting operations in 2018, versus just 35% in 2017, the practice is undoubtedly growing in scope and popularity. However, this begs the question: what's holding back the remaining majority -the other 57% -of organizations? The reality is that although many teams want to threat hunt, they simply don't know how to get started, or erroneously believe that they don't have the personnel, time, and resources to dedicate to the endeavor. But fortunately, that's no longer the case...
Know everything. About every endpoint. Right now.
Cisco recently rolled out a powerful new advanced threat hunting and investigation capability in Cisco? AdvancedMalware Protection (AMP) for Endpoints called Advanced Search that gives users the ability to search across all endpoints for forensic information and malware artifacts. Think of this as the ultimate search engine for all your endpoints -with over a hundred pre-canned queries provided, Advanced Search makes security investigations and threat hunting simple by allowing you to quickly run complex queries on hundreds of attributes in near real-time on any or all endpoints. For example, it allows you to type in queries like:
Advanced Search gives you deep visibility into what's happening on any endpoint at any time by taking a snapshot of its current state, and the search options are limitless; users can immediately perform advanced searches via the 100+ curated queries that come with the tool or create their own custom queries. Whether you're threat hunting, conducting an incident investigation, IT operations, or vulnerability and compliance assessments, Advanced Search gets you the answers you need about your endpoints fast.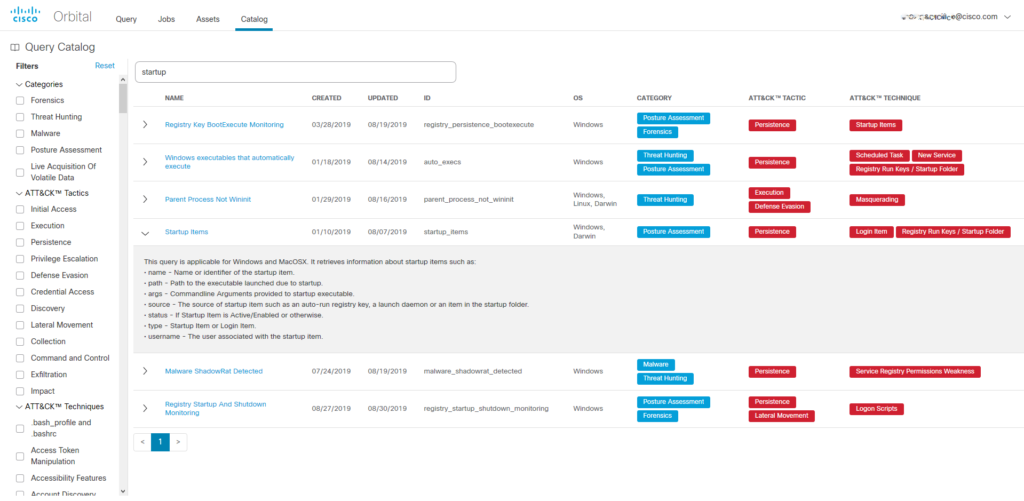
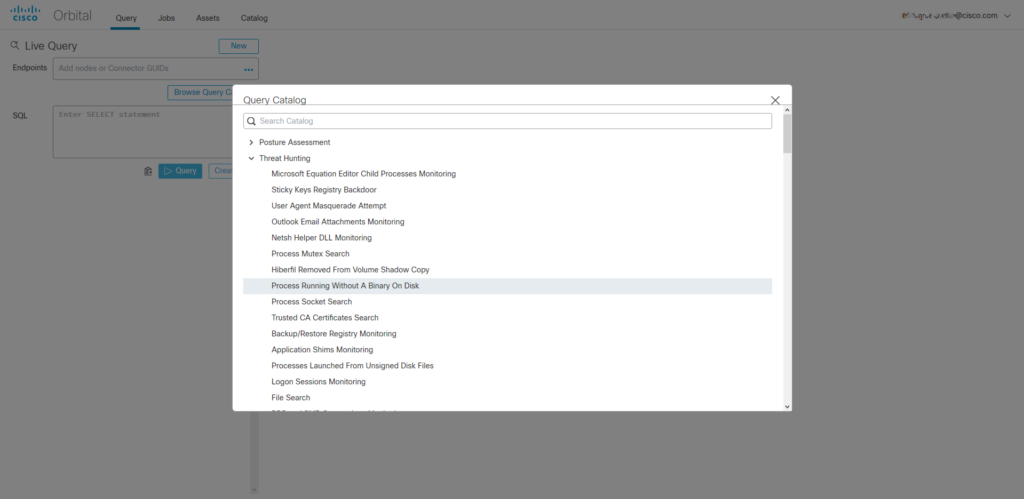
How does it work?
Whether you are investigating an incident or proactively hunting for threats Advanced Search can help you simplify and accelerate these tedious processes in the following ways:
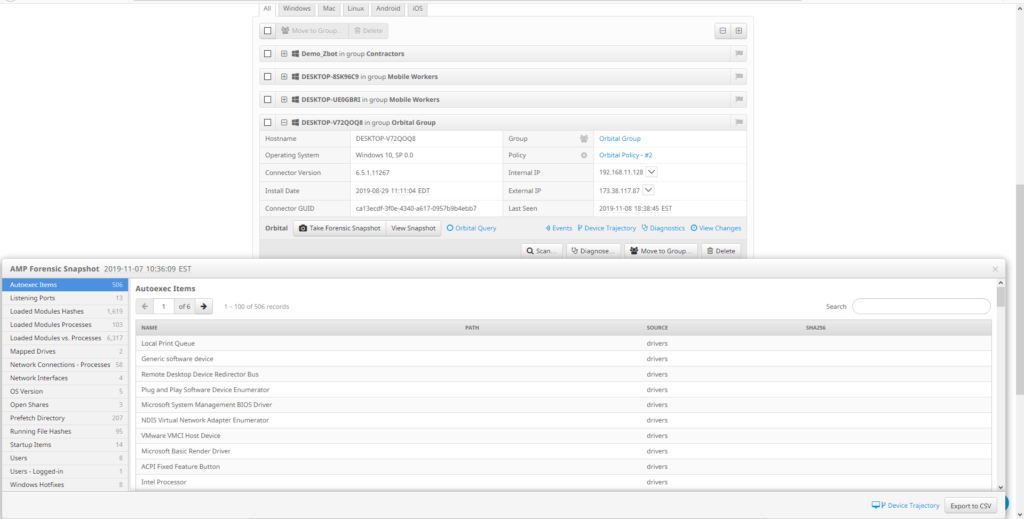
Common use cases
Advanced Search can help you do the following important tasks better, faster:
Threat Hunting Versus Incident Response
An additional bonus to threat hunting is that it breeds familiarity with tools and techniques that come into play when an incident or breach does occur, effectively training teams to be better incident responders. Since both disciplines deal directly with threats in your environment, the skills exercised when threat hunting are arguably one and the same as those associated with incident response. The only difference is that whereas incident response is reactive and involves known evidence of a threat in your environment, threat hunting is a proactive practice that is carried out without evidence. Since practicing threat hunting sharpens investigative skills and response times, teams that threat hunt are naturally better equipped to react like pros when faced with real incidents. The 'Hunting for hidden threats' whitepaper in Cisco's Cybersecurity Report Series covers this topic in more detail and is a great place to learn even more.
Whether you're new to threat hunting, are a seasoned veteran who wants to streamline operations and take your threat hunting program to the next level, or merely want to accelerate incident remediation, the solution to your woes has arrived. Test drive Advanced Search today with a free trial of Cisco AMP for Endpoints, or register for one of our Threat Hunting Workshops to get hands-on experience threat hunting, investigating, and responding to threats so that you can become a pro at finding the malicious needles in your digital haystacks.
 Горячие метки:
incident response
endpoint security
Cisco Secure Endpoints
Cisco Threat Response
Endpoint Detection and Response (EDR)
threat hunting
osquery
Next Generation Antivirus (NGAV)
Forensic investigations
Горячие метки:
incident response
endpoint security
Cisco Secure Endpoints
Cisco Threat Response
Endpoint Detection and Response (EDR)
threat hunting
osquery
Next Generation Antivirus (NGAV)
Forensic investigations