


Описание проблемы
Users are asking how to change USG to Layer 2 mode networking.
Для решения проблемы
The USG2200 series interfaces are all in Layer 3 mode. Since all USG2200 series interfaces themselves work in Layer 3, changing the interface will cause the web interface to be unable to log in, and then the configuration of Layer 2 transparent mode needs to be operated under the console port. The configuration method is as follows:
USG interface works in Layer 2 mode (transparent mode)
USG uses this networking to access the upstream and downstream networks without changing the topology of the original network or reassigning additional service addresses.
Networking Requirements
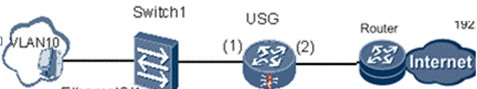
USG is deployed as a security device on the service node, the upstream device is a router, the downstream device is a switch, and the service interface works in the switching mode.
The organization diagram is shown in Figure 1, and the network is planned as follows:
- The segment address of the internal network is 192.168.1.0/24, which is connected to the GigabitEthernet 0/0/1 interface of the USG and is deployed in the trust area.
- The external network is connected to the GigabitEthernet 0/0/2 interface of the USG and is deployed in the Untrust area.
- The USG's management address is 192.168.1.2/24
Figure 1: Network diagram of service interfaces working at Layer 2 with upstream and downstream connected switches
Идеи по настройке
1. USG interfaces GigabitEthernet 0/0/1 and GigabitEthernet 0/0/2 both work in the switching mode, and join different security zones. 2.
2. create a VLANif interface on the USG and configure the management ip address to be 192.168.0.1.
3. configure the default route to the router on the USG.
4. configure interdomain packet filtering rules for the Trust area and Untrust area on the USG.
3. Процедура
1. Complete the following basic configuration on the USG.
#Configure GigabitEthernet 0/0/1 to work in switching mode.
<USG_A> system-view
[USG_A] interface GigabitEthernet 0/0/1
[USG_A-GigabitEthernet0/0/3] portswitch
[USG_A-GigabitEthernet0/0/3] quit
#Configure GigabitEthernet 0/0/1 to join the Trust area.
[USG_A] firewall zone trust
[USG_A-zone-trust] add interface GigabitEthernet 0/0/1
[USG_A-zone-trust] quit
#Configure GigabitEthernet 0/0/2 to work in switching mode.
[USG_A] interface GigabitEthernet 0/0/2
[USG_A-GigabitEthernet0/0/2] portswitch
[USG_A-GigabitEthernet0/0/2] quit
#Configure GigabitEthernet 0/0/2 to join the Untrust zone.
[USG_A] firewall zone untrust
[USG_A-zone-untrust] add interface GigabitEthernet 0/0/2
[USG_A-zone-untrust] quit
2.#Configure the management IP address of the USG.
[USG_A] interface vlianif 1
[USG_A-GigabitEthernet0/0/1] ip address 192.168.0.2 24
[USG_A-GigabitEthernet0/0/1] quit
[USG_A] firewall zone untrust
[USG_A-zone-untrust] add interface vlanif 1
3.#Configure the default route from the USG to the router.
[USG_A] ip route-static 0.0.0.0 0.0.0.0 192.168.0.1
4.#Release all inter-area packet filtering by default.0.0.0.0.0.0.0.0.0.0.0.
[USG_A] firewall packet-filter default permit all
 Горячие метки:
3. Хуавей
Горячие метки:
3. Хуавей
Зарегистрируйтесь по электронной почте сейчас для еженедельной акции акции
100% free, Unsubscribe any time!
Add 1: Room 605 6/F FA YUEN Commercial Building, 75-77 FA YUEN Street, Mongkok KL, HongKong Add 2: Room 405, Building E, MeiDu Building, Gong Shu District, Hangzhou City, Zhejiang Province, China
Whatsapp/ тел: +8618057156223 * телефон: *: 0086 571 86729517 Tel in HK: 00852 66181601
Электронная почта: [email protected]
 English
English Pусский
Pусский Français
Français Español
Español Português
Português