































Bruce Schneier, the security technologist and author famously said, "Complexity is the worst enemy of security."
We have been working with some customers who agree strongly with this sentiment because they have been struggling with increasing complexity in their access control lists and firewall rules.
Typical indicators of operational complexity have been:
Virtualization tends to result in larger numbers of application servers being defined in rule sets. In addition, we are seeing that some customers need to define new policies to distinguish between BYOD and managed endpoint users as part of their data center access controls. At the same time, in many environments, it is rare to find that rules are efficiently removed because administrators find it difficult to ascertain that those rules are no longer required. The end result is that rule tables only increase in size.
TrustSec is a solution developed within Cisco, which describes assets and resources on the network by higher-layer business identifiers, which we refer to as Security Group Tags, instead of describing assets by IP addresses and subnets.
Those of us working at Cisco on our TrustSec technology have been looking at two particular aspects of how this technology may help remove complexity in security operations:
While originally conceived as a method to provide role-based access control for user devices or accelerate access control list processing, the technology is proving of much broader benefit, not least for simplifying firewall rule sets.
For example, this is how we can use Security Group Tags to define access policies in our ASA platforms:
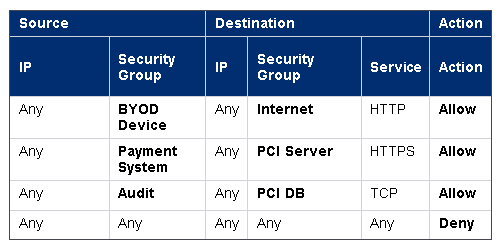
Being able to describe systems by theirbusiness role, instead of where they are on the network, means that servers as well as users can move around the network but still retain the same privileges.
In typical rule sets that we have analyzed, we discovered that we can reduce the size of rule tables by as much as 60-80% when we use Security Group Tags to describe protected assets. That alone may be helpful, but further simplification benefits arise from looking at the actual policies themselves and how platforms such as the Cisco Adaptive Security Appliance (ASA) can use these security groups.
In terms of incident response and analysis, customers are also finding value in the ability to administratively change the Security Group Tag assigned to specific hosts, in order to invoke additional security analysis or processing in the network.
By removing the need for complex rule changes to be made when server moves take place or network changes occur, we are hoping that customers can save time and effort and more effectively meet their compliance goals.
For more information please refer to www.cisco.com/go/trustsec.
Follow @CiscoSecurity on Twitter for more security news and announcements.
 Горячие метки:
Безопасность и охрана
BYOD
Соединенные Штаты америки
Управление по техническому сотрудничеству
Security Group tags
Горячие метки:
Безопасность и охрана
BYOD
Соединенные Штаты америки
Управление по техническому сотрудничеству
Security Group tags