































 Trend Micro Zero Day Initiative
Trend Micro Zero Day Initiative The Zero Day Initiative (ZDI), a vulnerability wholesaler, has reduced its disclosure timelines for incomplete patches in a bid to push vendors into improving the quality of their security updates.
ZDI, a brand owned by security firm Trend Micro, is making the move because of what says is a "disturbing" decrease in patch quality and a rise in vague communications about patches.
The impact on enterprises is that they can't accurately estimate the risk to their systems and they're wasting money on applying incomplete patches that are re-released down the track and need re-applying a second time around.
ZDI's standard disclosure timeline gives software vendors 120 days to release a patch, but it's now introducing shorter timelines for "failed patches" that it will be monitoring.
"Moving forward, we will be tracking failed patches more closely and will make future policy adjustments based on the data we collect," says Brian Gorenc, senior director of ZDI.
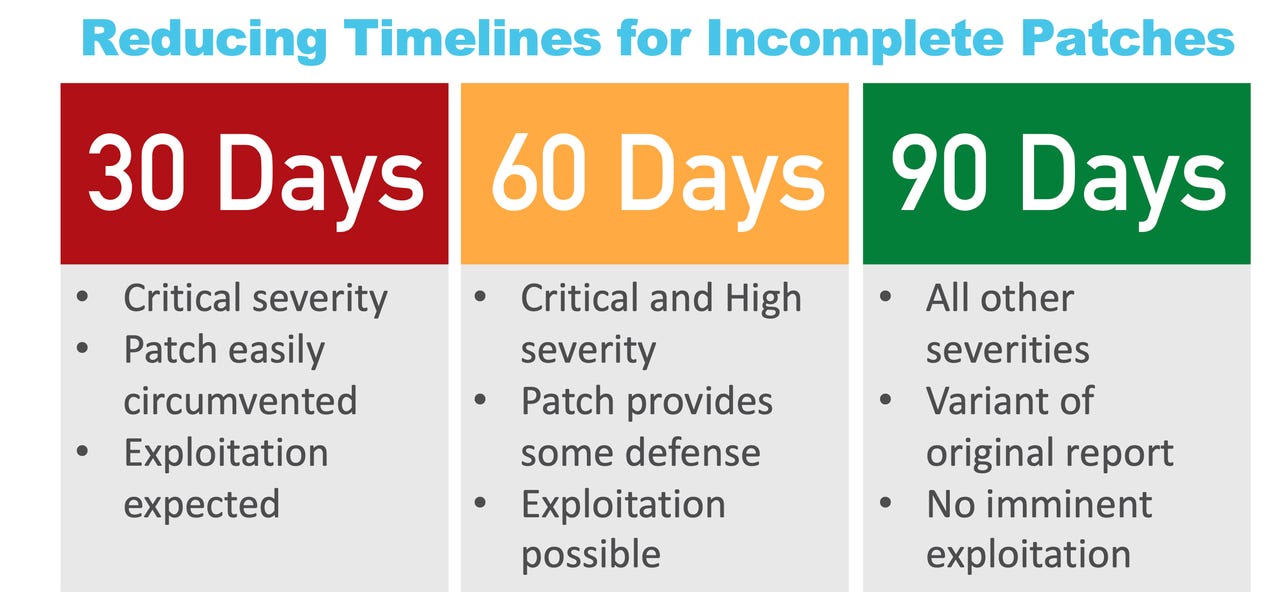
For failed patches, ZDI will give vendors 30 days to address the flaw if it's critical, the patch is easily circumvented, and if exploitation is expected. Vendors will have 60 days to address critical and high severity issues if the patch provides some defence and exploitation is possible. They will get 90 days for all other vulnerabilities below these severity ratings and there's no imminent threat of exploitation.
"Over the last few years, we've noticed a disturbing trend -a decrease in patch quality and a reduction in communications surrounding the patch. This has resulted in enterprises losing their ability to accurately estimate the risk to their systems. It's also costing them money and resources as bad patches get re-released and thus re-applied," Gorenc says in a blogpost.
Google Project Zero researcher Maddie Stone has also called out software vendors for releasing incomplete patches. She estimated half of the 18 zero-day or previously undisclosed flaws in the first half of 2022 could have been avoided with more comprehensive patching and regression tests. Some of those bugs are fixed initially but regress over time.
Because the root cause issue was not addressed, attackers were able to revisit and expose the original vulnerability through a different path, she said.
Stone's analysis of 24 zero-days in 2020 revealed that six were variants of previously disclosed vulnerabilities, and three were incompletely patched vulnerabilities. As she pointed out, incomplete patches make it easier for attackers to exploit users with zero-days.
It's not just the quality of patches but the lack of information vendors provide about vulnerabilities. Via Dark Reading, ZDI's Dustin Childs is critical of Microsoft's decision in 2020 to remove executive summaries in its Security Update Guide (SUG) each Patch Tuesday. In its place, iMicrosoft only makes available Common Vulnerability Severity Scale (CVSS) scores on a scale of 0 to 10.
In a talk at Black Hat 2022, Childs said that defenders lose the context they used to have to determine risk, along with details about, for example, what security feature was bypassed.
He also estimated that in ZDI's program, which has disclosed 10,000 bugs since 2005, between 10% to 20% of the bugs researchers analyse are due to a faulty or incomplete patch.
Childs also drew attention to the reality that each Common Vulnerabilities and Exposures (CVE) identifier does not equate to a single vulnerability. Vendors often report that an update with a single CVE addresses multiple security issues.
 Горячие метки:
Технологии и оборудование
Безопасность и охрана
Горячие метки:
Технологии и оборудование
Безопасность и охрана