































Nonprofit foundation Open Web Application Security Project (OWASP) has released an updated draft of its ranking of the top 10 vulnerabilities, the first changes to the list since November 2017.
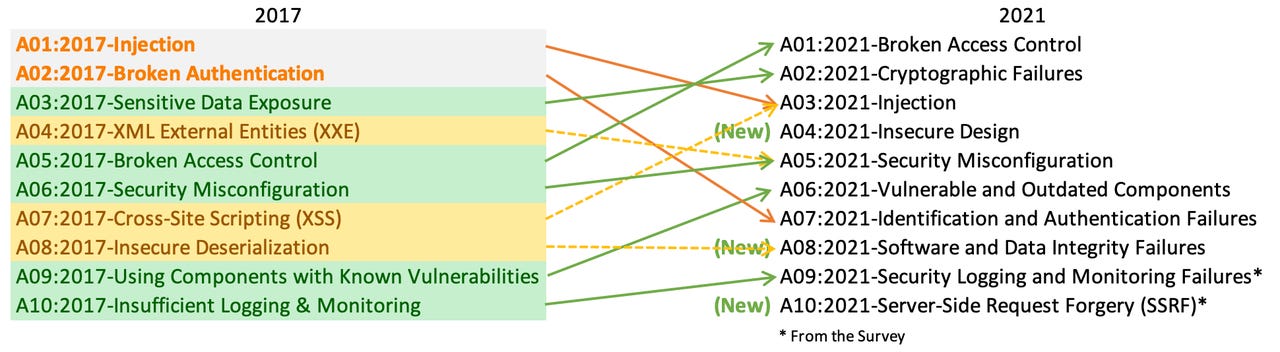
The new list features considerable changes, including the emergence of Broken Access Control, which moved from fifth on the list to number 1. The organization said 94% of applications have been tested for some form of broken access control, and "the 34 CWEs mapped to Broken Access Control had more occurrences in applications than any other category."
Cryptographic Failures also moved up the list to number 2 due to its connection to sensitive data exposure and system compromise. Injection moved down to the third spot, but OWASP noted that 94% of the applications were tested for some form of injection, which now includes cross-site scripting.
A new category -- Insecure Design -- made its way into the fourth spot on the list, followed by Security Misconfiguration, which moved up one spot compared to the 2017 list.
Security Misconfiguration now includes external entities. The lists' authors said it was not surprising considering 90% of applications were tested for some form of misconfiguration and that there have been more shifts to highly configurable software.
Vulnerable and Outdated Components was ranked number 9 in 2017 but moved up to number 6 for this year's ranking.
"It is the only category not to have any CVEs mapped to the included CWEs, so a default exploit and impact weights of 5.0 are factored into their scores," the lists' authors noted.
 OWASP
OWASP Identification and Authentication Failures -- previously called Broken Authentication -- fell significantly from number 2 to 7, with OWASP explaining that the increased availability of standardized frameworks has helped in addressing it.
Software and Data Integrity Failures is an entirely new category for 2021 and focuses primarily on assumptions related to software updates, critical data, and CI/CD pipelines without verifying integrity.
"One of the highest weighted impacts from CVE/CVSS data mapped to the 10 CWEs in this category. Insecure Deserialization from 2017 is now a part of this larger category," OWASP said.
Security Logging and Monitoring Failures was previously last on the list but moved up one spot and has expanded to include other types of failures. While these are challenging to test for, they can "directly impact visibility, incident alerting, and forensics."
Last on the list is Server-Side Request Forgery, which has a "relatively low" incidence rate but was cited highly by industry professionals.
OWASP said that overall, there were three new categories and four others that had either name or scope changes made for the 2021 list. OWASP, which has put the list together for more than a decade, compiles the list based on contributed data and industry surveys.
"We do this for a fundamental reason; looking at the contributed data is looking into the past. AppSec researchers take time to find new vulnerabilities and new ways to test for them. It takes time to integrate these tests into tools and processes," OWASP said.
"By the time we can reliably test a weakness at scale, years have likely passed. To balance that view, we use an industry survey to ask people on the front lines what they see as essential weaknesses that the data may not show yet."
Ben Pick, senior application security consultant at nVisium and one of the Northern Virginia OWASP Chapter leaders, toldZDNetthat the OWASP Top 10 is not intended to be used for compliance purposes. Still, it is often looked at in this manner.
"The items currently listed are meant to drive awareness of trends across the industry regarding vulnerabilities and exploits faced by the companies who volunteered their data - particularly for those who may not have a security background," Pick explained.
"Overall, this living document matches the risks I have observed within various assessments, and I will continue to use this resource to learn about new types of threats. The OWASP Top 10 is still in draft form and will be edited and improved as more of the security industry reviews the content."
Jayant Shukla, CTO of K2 Cyber Security, added that instead of old risks going away, OWASP had consolidated existing risks into several categories, and new risks have been added, reflecting the increased threats facing web applications.
Shukla noted that one of the reasons Server-Side Request Forgery attacks authentication issues are becoming more severe is because of the rapid increase in the use of microservices in building applications.
"These new risk categories emphasize the need to shift left and improve pre-production testing. Unfortunately, these problems are often hard to find during testing, and sometimes they arise and are only a problem when different application modules interact, making them even harder to detect," Shukla said.
"In fact, the National Institute of Standards and Technologies has recognized these shortcomings, and last year updated their SP800-53 application security framework to include Runtime Application Self Protection and Interactive Application Security Testing to better protect against these critical software weaknesses. It's time the software development industry got on board and adopted these more effective technologies."
 Горячие метки:
Технологии и оборудование
Безопасность и охрана
Горячие метки:
Технологии и оборудование
Безопасность и охрана