

























As a business or technical leader, you know you need to protect your company in a rapidly evolving mobile ecosystem.
However, threats are not always obvious. As malware and attacks become more sophisticated over time, business decision makers must work with technical decision makers to navigate security threats in a mobile world.
I'm excited to introduce a new blog series, authored by Kathy Trahan, which will explore the topic of enterprise mobility security from a situational level and provide insight into what leaders can do now to mitigate risk.
This first post will discuss the security concerns presented by the rapid-fire growth of BYOD (Bring Your Own Device) and how implementing specific policies can help organizations reap the benefits of true mobility now and in the future.
 Kathy Trahan
Kathy Trahan With the increasing amount of tablets, wearables, and other connected "things" in the workplace, it's no wonder that the BYOD trend is causing a dynamic shift in security policies and protocol.
This heightened focus on security only increases when the security threat evolution shows that attackers seem to stay one step ahead of the security measures in place to stop them. And while the BYOD movement does present special challenges to ensuring data security, it also affords BDMs and TDMs an opportunity to collaborate and come up with security solutions that balance the need to secure company assets while still allowing employees to conduct business on devices that are familiar and comfortable to them.
As enterprises look for ways to improve productivity, efficiency, and flexibility for their workforces, mobility has become a key factor. A Gartner survey predicts that by 2017, half of employers will require their employees to provide their own devices for work purposes. And as use of and reliance on mobility increase, so does the need for security policies that allow employees to function in a work world that extends beyond their cubicle and office walls.
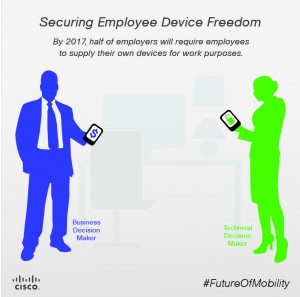
Operating from different perspectives when it comes to innovation, BDMs and TDMs must ask themselves three key questions when it comes to security and giving employees the freedom to use their mobile devices:
Question#1: What is our mobile security policy?
The first step is conducting a review of the company's current security policy when it comes to off-site access.
A recent study reveals that 80 percent of corporate security professionals and IT leaders recognize that "end user carelessness" is the largest security threat to any organization. A clear and concise security policy outlines all the precautions that mobile device users must adhere to, from the simple (password encryption on a cell phone) to the more complex (allowing only management-level employees to access certain networks after traditional work hours).
BDMs must ensure employees can stay productive, and TDMs have the responsibility to ensure mobile policies are followed. Determining guidelines regarding where devices can be taken, incorporating password-protected networks, controlling what information can be accessed, and enforcing these rules are essential to reduce risk. Ideally, a mobile security policy should be transparent to the end users, allowing them to focus on their work while protecting the company.
Question#2: What platform or devices are best for our business?
The device landscape has changed. In years past, employees simply had to choose from a relatively small list of devices the company would pay for. Now, employees want to use their own personal devices, increasing the risk of a security breach when corporate-issued devices are no longer the standard. And with wearables becoming more popular, security threats have an entirely new avenue to invade.
When it comes to offering the best technology for the BYOD policy, deciding which devices and platforms (Apple, Android, or both, for example) an organization will support is an important step for both BDMs and TDMs to take. After choosing the supported mobile devices, what constitutes a trusted mobile device? Such questions as-Do we require the latest OS? Do we require all work-related traffic from a mobile device to be encrypted? BDMs have the company's bottom line to consider when choosing the most cost-effective providers and services, but this must also be aligned with TDMs and with their department resources and capabilities to monitor security threats.
Question#3: How much access will these mobile devices have to our business?
When employees use their mobile devices for both personal and business use, privacy and content-control questions may arise. TDMs can present a valid argument that they must be able to wipe a phone clean if an employee loses a mobile device or is terminated, but BDMs will likely hear feedback regarding privacy and exactly which IT departments have access to personal devices.
Exerting control over employee-owned devices is not an easy path to navigate, but one that is necessary to protect the integrity of company information. The best-practice solution for companies will differ. Employers may purchase devices and maintain full access, or companies may ensure they can remotely restrict access if an employee is no longer allowed access to the organization's network. Employers may decide to segment and control mobile access to corporate resources only and hold no responsibility for employees' personal applications and data. Whatever the solution may be, BDMs and TDMs must carefully consider the employee need for privacy weighed against the business need to protect sensitive information.
BYOD will continue to change how enterprises operate and how the workforce becomes more influential toward best practices. As such, BDMs and TDMs have to step out of their silos and begin to see one another as collaborative partners. Finding balance is imperative and both must rise to the occasion to keep their business competitive.
For more information about the BYOD's role in a holistic enterprise mobility strategy, follow @Cisco_Mobility on Twitter and join the conversation#FutureOfMobility.
Additional resources:
 Горячие метки:
Безопасность и охрана
B. мобильность
future of mobility
Устройство для сбора
Security Threats
Горячие метки:
Безопасность и охрана
B. мобильность
future of mobility
Устройство для сбора
Security Threats