































 Image: Google
Image: Google Google has published a new ransomware report, revealing Israel was far and away the largest submitter of samples during that period.
The tech giant commissioned cybersecurity firm VirusTotal to conduct the analysis, which entailed reviewing 80 million ransomware samples from 140 countries.
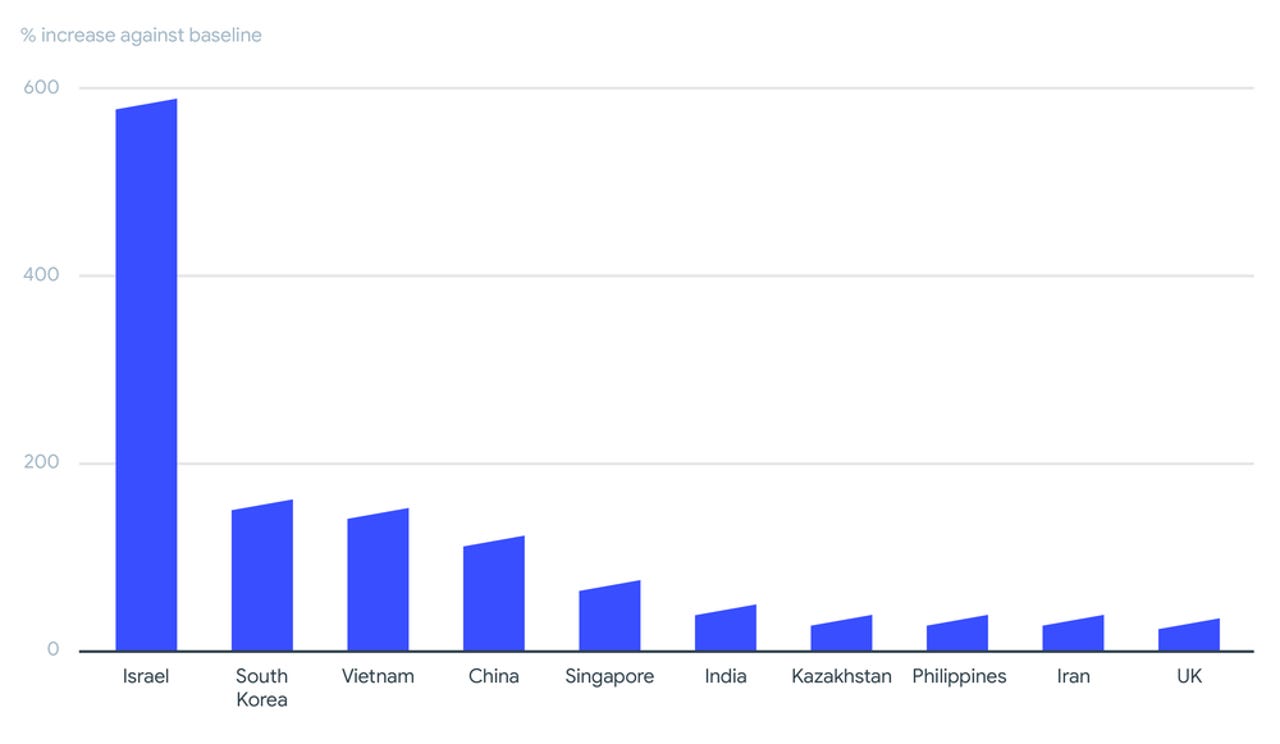
According to the report [PDF], Israel, South Korea, Vietnam, China, Singapore, India, Kazakhstan, Philippines, Iran and the UK were the 10 most affected territories based on the number of submissions reviewed by VirusTotal.
Israel had the higher number of submissions and that amount was a near-600% increase from its baseline amount of submissions. The report did not state what Israel's baseline amount of submissions was during that period.
From the start of 2020, ransomware activity was at its peak during the first two quarters of 2020, which VirusTotal attributed to activity by ransomware-as-a-service group GandCrab.
"GandCrab had an extraordinary peak in Q1 2020 which dramatically decreased afterwards. It is still active but at a different order of magnitude in terms of the number of fresh samples," VirusTotal said.
There was another sizeable peak in July 2021 that was driven by the Babuk ransomware gang, a ransomware operation that was launched at the beginning of 2021. Babuk's ransomware attack generally features three distinct phases: Initial access, network propagation, and action on objectives.
GandCrab was the most active ransomware gang since the start of 2020, accounting for 78.5% of samples. GandCrab was followed by Babuk and Cerber, which accounted for 7.6% and 3.1% of samples, respectively.
According to the report, 95% of ransomware files detected were Windows-based executables or dynamic link libraries (DLLs) and 2% were Android-based.
The report also found that exploits consisted of only a small portion of the samples -- 5%.
"We believe this makes sense given that ransomware samples are usually deployed using social engineering and/or by droppers (small programs designed to install malware)," VirusTotal said.
"In terms of ransomware distribution attackers don't appear to need exploits other than for privilege escalation and for malware spreading within internal networks."
After reviewing the samples, VirusTotal also said that there was a baseline of between 1,000 and 2,000 first-seen ransomware clusters at all times throughout the analysed period.
"While big campaigns come and go, there is a constant baseline of ransomware activity that never stops," it said.
 Горячие метки:
Технологии и оборудование
Безопасность и охрана
Горячие метки:
Технологии и оборудование
Безопасность и охрана