































Researchers have uncovered a new infostealer malware being peddled in Russian underground forums.
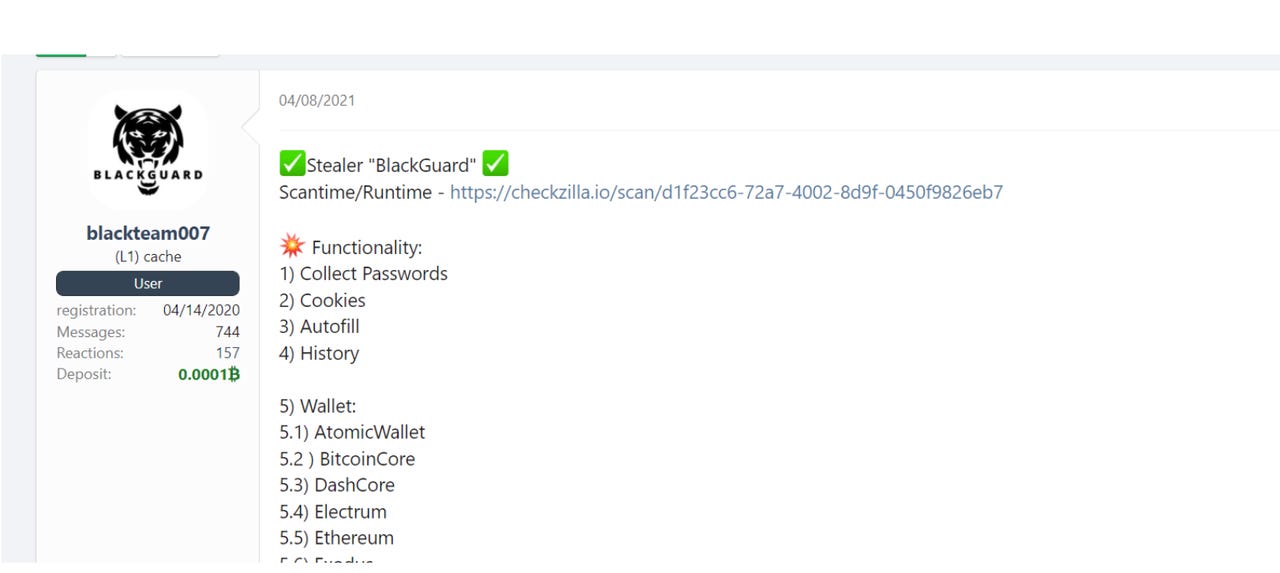
Dubbed BlackGuard, zScaler says that the new malware strain is "sophisticated" and has been made available to criminal buyers for a monthly price of$200.
Infostealers are forms of malware designed to harvest valuable data, potentially including operating system information, contact lists, screenshots, network traffic, and online account credentials including those used to access financial services and banking.
A range of malicious software and exploit kits are sold every day underground, some of which are purchased outright. In contrast, others are offered on a malware-as-a-service (MaaS) basis: subscribers pay on a weekly, monthly, or yearly basis, and the developer keeps their malicious creations updated in return.
Perhaps to build a customer base for this malware, or to generate cash quickly, BlackGuard is also being sold for$700 in return for a lifetime subscription.
 zScaler
zScaler According to the cybersecurity researchers, BlackGuard can steal information, including saved browser credentials and history, email client data, FTP accounts, autofill content, conversations in messenger software, cryptocurrency credentials, and other account information. Messengers targeted include Telegram, Signal, Tox, Element, and Discord.
Simple steps can make the difference between losing your online accounts or maintaining what is now a precious commodity: Your privacy.
Read nowWhen it comes to cryptocurrency theft, the malware will target files such as wallet.dat that may contain wallet addresses and private keys. BlackGuard may also go after Chrome and Edge cryptocurrency wallet browser extensions.
Written in .NET, the infostealer is still in active development but is already equipped with a crypto-based packer, base64 decoding, obfuscation, and antibugging capabilities to make reverse-engineering more difficult.
Once it lands on a vulnerable machine, the malware will also check the operating system's processes and will try to stop any activities related to antivirus software or sandboxing.
The infostealer is also selective when it comes to its targets. For example, the malware will exit if the OS appears to be located in a CIS country, such as Russia, Belarus, or Azerbaijan.
If an exit isn't necessary, the infostealer then grabs all of the information it can, packages it up into a .zip archive, and sends it to a command-and-control (C2) server through a POST request.
"While applications of BlackGuard are not as broad as other stealers, BlackGuard is a growing threat as it continues to be improved and is developing a strong reputation in the underground community," the researchers say.
Infostealers can be used on their own or packaged up with other forms of malware, such as Trojans or ransomware variants.
In other malware news, researchers from Aqua Security have recently uncovered a new strain of ransomware designed to target Jupyter Notebook environments.
Have a tip?Get in touch securely via WhatsApp Signal at +447713 025 499, or over at Keybase: charlie0
 Горячие метки:
Технологии и оборудование
Безопасность и охрана
Горячие метки:
Технологии и оборудование
Безопасность и охрана