































Okta says that a rapid investigation into the sharing of screenshots appearing to show a data breach has revealed they relate to a "contained" security incident that took place in January 2022.
Okta, an enterprise identity and access management firm, launched an inquiry after the LAPSUS$hacking group posted screenshots on Telegram that the hackers claimed were taken after obtaining access to "Okta.com Superuser/Admin and various other systems."
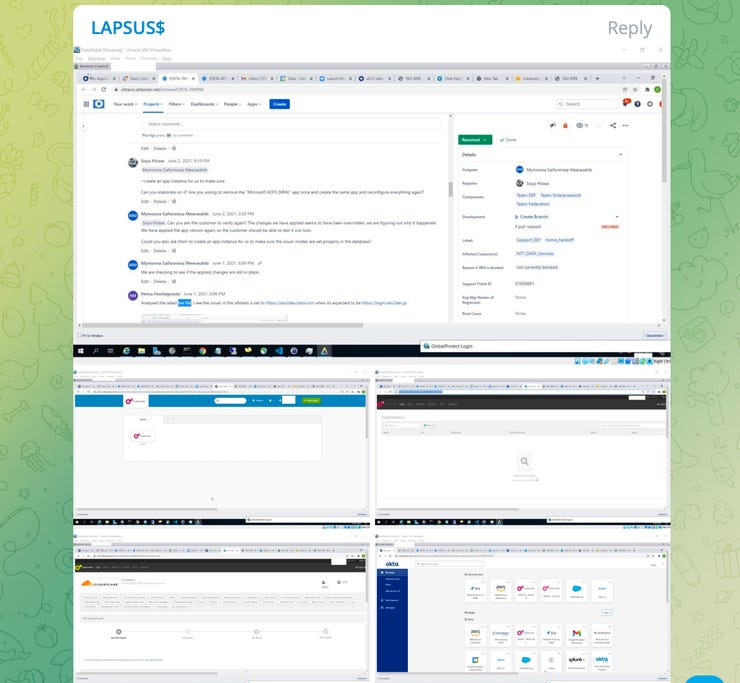 Screenshot via Telegram
Screenshot via Telegram The images were shared over Telegram and various social media networks this week.
"For a service that powers authentication systems to many of the largest corporations (and FEDRAMP approved) I think these security measures are pretty poor[...]," LAPSUS$said. "Before people start asking, we did not access/steal any databases from Okta -- our focus was only on Okta customers."
In an emailed statement on Tuesday, Okta said the screenshots shared online "appear to be connected to a security event in late January."
Okta said:
"In late January 2022, Okta detected an attempt to compromise the account of a third-party customer support engineer working for one of our subprocessors. The matter was investigated and contained by the subprocessor. We believe the screenshots shared online are connected to this January event."
"Based on our investigation to date, there is no evidence of ongoing malicious activity beyond the activity detected in January," Okta added.
In a tweet, Cloudflare CEO Matthew Prince added to the discussion, commenting:
"We are aware that Okta may have been compromised. There is no evidence that Cloudflare has been compromised. Okta is merely an identity provider for Cloudflare. Thankfully, we have multiple layers of security beyond Okta, and would never consider them to be a standalone option."
Lapsus$is a hacking group that has quickly raised itself through the ranks by allegedly breaking into the systems of high-profile companies, one after the other, in order to steal information and threaten to leak it online unless blackmail payments are made.
Recent breaches connected to the group include those experienced by Samsung, Nvidia, and Ubisoft.
On Sunday, a screenshot was shared that suggested an alleged Microsoft breach may have taken place, potentially via an Azure DevOps account, although the post has since been deleted. Microsoft is investigating.
Based in San Francisco, Okta is a publicly-traded company with thousands of customers, including numerous technology vendors. The company accounts for FedEx, Moody's, T-Mobile, JetBlue, and ITV among its clients.
"Lapsus$is known for extortion, threatening the release of sensitive information, if demands by its victims are not made," commented Ekram Ahmed, spokesperson at Check Point. "The group has boasted breaking into Nvidia, Samsung, Ubisoft and others. How the group managed to breach these targets has never fully been clear to the public. If true, the breach at Okta may explain how Lapsus$has been able to achieve its recent string [of] successes."
Update 19.07GMT: Okta has provided further details of the cybersecurity incident. In an updated statement, the technology vendor said "Okta service has not been breached and remains fully operational. There are no corrective actions that need to be taken by our customers."
Okta also said that during the January incident, the impacted customer support engineer's account was quickly suspended while a third-party cyberforensics firm investigated the issue.
"Following the completion of the service provider's investigation, we received a report from the forensics firm this week," Okta said. "The report highlighted that there was a five-day window of time between January 16-21, 2022, where an attacker had access to a support engineer's laptop."
The company commented:
"The potential impact to Okta customers is limited to the access that support engineers have. These engineers are unable to create or delete users, or download customer databases. Support engineers do have access to limited data -- for example, Jira tickets and lists of users -- that were seen in the screenshots. Support engineers are also able to facilitate the resetting of passwords and multi-factor authentication factors for users, but are unable to obtain those passwords."
Okta's investigation is ongoing. The company added that there is no impact to Auth0, HIPAA, or FedRAMP customers.
Update 7.39am GMT 23/3:Okta has now revised its estimate to potentially impact 2.5% of customers.
Have a tip?Get in touch securely via WhatsApp Signal at +447713 025 499, or over at Keybase: charlie0
 Горячие метки:
Технологии и оборудование
Безопасность и охрана
Горячие метки:
Технологии и оборудование
Безопасность и охрана