















Researchers say that malicious Android applications disguised as legitimate shopping apps are stealing Malaysian bank customers' financial data.
A roundup of the best software and apps for Windows and Mac computers, as well as iOS and Android devices, to keep yourself safe from malware and viruses.
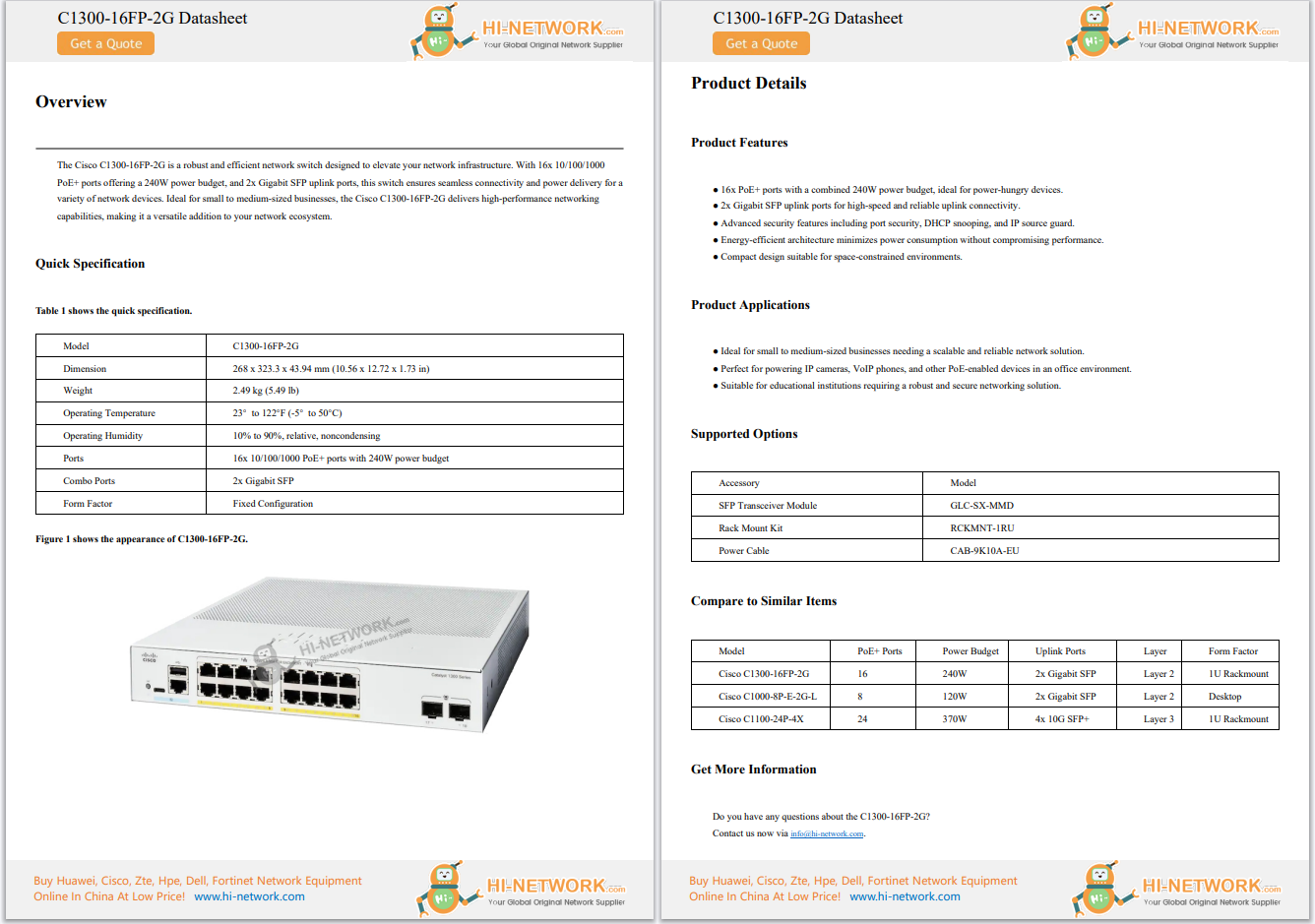
Read nowOn Wednesday, ESET's cybersecurity team published new research documenting three separate apps targeting customers who belong to eight Malaysian banks.
First identified in late 2021, the attackers began by distributing a fake app pretending to be Maid4u, a legitimate cleaning service brand. The cyberattackers responsible created a website with a similar name -- a technique known as typosquatting -- and tried to lure potential victims into downloading the malicious Maid4u app.
Paid Facebook Ads were used to further the domain's appearance of legitimacy and to work as a distribution method.
In January, MalwareHunterTeam shared a further three websites operating in the same vein, and at the time of writing, the campaign is still ongoing. ESET has since found another four malicious websites that mimic legitimate Malaysian shopping and cleaning services.
Grabmaid, Maria's Cleaning, Maid4u, YourMaid, Maideasy, and MaidACall are all being impersonated alongside PetsMore, a pet shop. Five of the abused services do not have an app on Google Play.
The malicious domains don't allow customers to purchase products or services directly. Instead, the attack vector is a button that claims to link to Google Play, Google's official app repository, for customers to pay through.
The fake Android apps linked to the purchase buttons are hosted on the attacker's servers. At this stage, a victim can avoid infection if they have chosen not to enable "Install unknown apps" -- a default security mechanism for Android handsets -- but if they install the software, they are shown different 'payment' options through the apps.
While two 'options' are displayed -- a credit card payment or a direct bank transfer -- the first option doesn't work. Left with bank transfers, victims are presented with a fake payment page that lists eight Malaysian banks: Maybank, Affin Bank, Public Bank Berhad, CIMB Bank, BSN, RHB, Bank Islam Malaysia, and Hong Leong Bank.
When users input their bank credentials, they are sent to the attacker's command-and-control (C2) server. The victim is then shown an error message.
"To make sure the threat actors can get into their victims' bank accounts, the fake e-shop applications also forward all SMS messages received by the victim to the operators in case they contain two-factor authentication (2FA) codes sent by the bank," the researchers added.
However, the malware embedded in these apps is simplistic: a basic info stealer and message forwarder. The lack of sophistication is highlighted as the apps can't intercept, hide, or delete the 2FA SMS messages from a victim's handset when an attacker tries to access their bank account, and so fraudulent access attempts may be flagged when 2FA codes are sent to the Android device.
One of the victim organizations being impersonated, MaidACall, has published a Facebook post warning its customers of the campaign.
"Currently, the campaign targets Malaysia exclusively, but it might expand to other countries and banks later on," ESET says. "Moreover, the attackers may also enable the theft of credit card information in the malicious apps in the future."
See also
Have a tip?Get in touch securely via WhatsApp Signal at +447713 025 499, or over at Keybase: charlie0
 Горячие метки:
Технологии и оборудование
Безопасность и охрана
Горячие метки:
Технологии и оборудование
Безопасность и охрана