



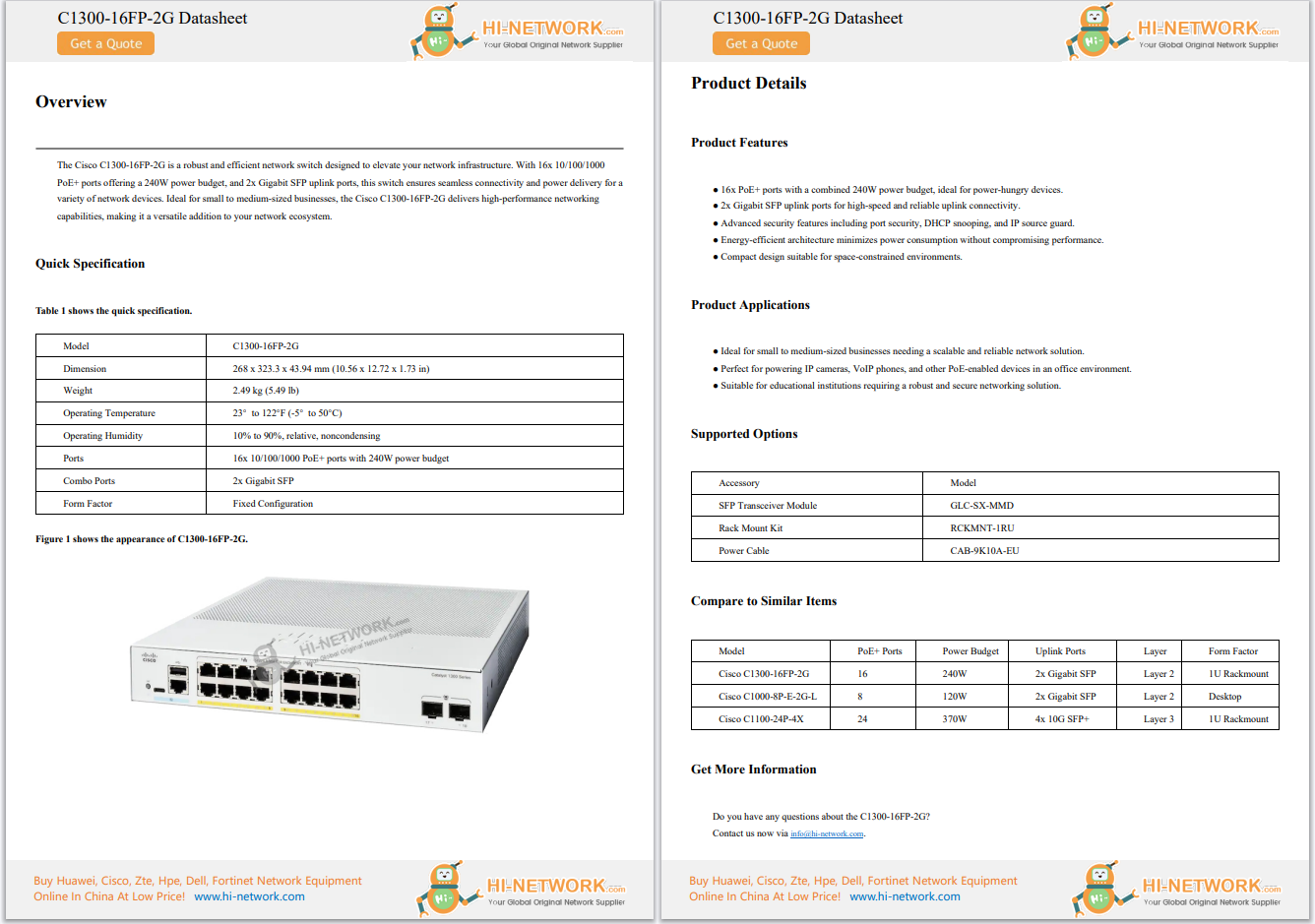












 Image: Getty/Erikona
Image: Getty/Erikona Highly skilled cyber attackers are using a never-before-seen technique to stealthily infect victims with malware by abusing legitimate tools.
The campaign has been detailed by cybersecurity researchers at Symantec, who say that the attackers can spend more than 18 months inside the networks of victims, all while taking steps to ensure their activity stays under the radar to avoid detection in what's thought to be an intelligence-gathering and espionage operation.
How the attack begins is still uncertain, but victims become infected with a previously undocumented form of malware dubbed Geppei, which is used to deliver another form of backdoor malware that has been named Danfuan, which provides secret access to compromised machines, along with the ability to snoop on data stored or entered on systems.
The attackers attempt to stay under the radar by installing backdoors on appliances that didn't support security tools, such as SANS arrays, load balancers, and wireless access point controllers.
Also: The scary future of the internet: How the tech of tomorrow will pose even bigger cybersecurity threats
What makes this campaign unique is the way Geppei abuses Internet Information Services (IIS) logs to remain undetected, something which researchers say they've not seen used in attacks before.
IIS logs form part of Windows server services and are commonly used for troubleshooting web applications, along with providing information on how users interact with websites and applications.
Geppei reads commands from a legitimate IIS log, which are meant to record data from IIS, such as web pages and apps. In this scenario, the attackers can send commands to a compromised web server by disguising them as web access requests and, while IIS logs them as normal, the trojan can read them as commands. The commands read by Geppei contain malicious encoded files that are saved to an arbitrary folder and they run as backdoors.
"The use of IIS logs by the attacker is one of the most interesting things about this campaign. The technique of reading commands from IIS logs is not something Symantec researchers have seen being used to date in real-world attacks," Brigid O Gorman, senior intelligence analyst at Symantec Threat Hunter Team, told .
The attacks are linked to a group that Symantec calls Cranefly -also known as UNC3524. Researchers suggest that the novel and exceedingly stealthy methods used in this campaign indicate that it's the work of a "fairly skilled threat actor" who is motivated by intelligence gathering.
"The development of custom malware and new tools requires a certain level of skills and resources that not all threat actors have, so it implies that those behind Cranefly have a certain level of skills that makes them capable of carrying out stealthy and innovative cyberattacks," said O Gorman.
Symantec hasn't linked the attacks to any particular attacker, but researchers at Mandiant have previously noted that methodologies used in campaigns by Cranefly/UNC3524 "overlapped with techniques used by multiple Russia-based espionage threat actors".
The campaign isn't widespread, but that doesn't mean it doesn't pose a danger to organizations -particularly as the campaign remains active and those behind it are adopting new techniques to hide attacks. However, there's action that can be taken to help prevent this attack and other malicious cyber campaigns.
"Organizations should adopt a defense in-depth strategy, using multiple detection, protection, and hardening technologies to mitigate risk at each point of a potential attack chain," recommends O Gorman.
Techniques that organizations can employ to help prevent or detect attacks include using two-factor authentication on accounts, adopting network segmentation, and avoiding the use of default passwords.
 Горячие метки:
Технологии и оборудование
Безопасность и охрана
Горячие метки:
Технологии и оборудование
Безопасность и охрана