















From craftily engineering social-phishing campaigns to infecting simple IoT devices, threat actors seek a single vulnerable point of entry to exploit an entire network of enterprise information treasures. Once an entry point is breached, lateral movement from device to device can spread in mere seconds. Ransomware, the bane of security teams, can infect thousands of end points, encrypting, erasing, and locking up the crucial components of business and government. That
 Горячие метки:
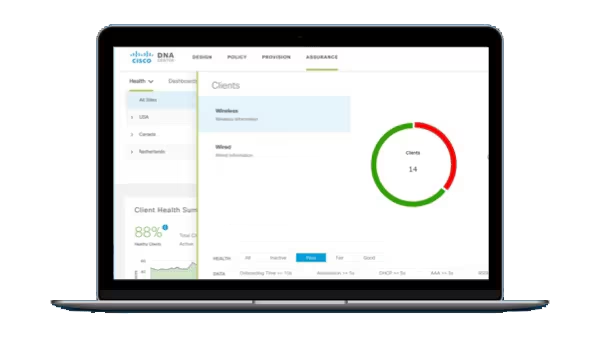
Циско центр ДНК
SD-Access
group-based policy
access security
2. Сегментация
AI Endpoint Analytics
Горячие метки:
Циско центр ДНК
SD-Access
group-based policy
access security
2. Сегментация
AI Endpoint Analytics