

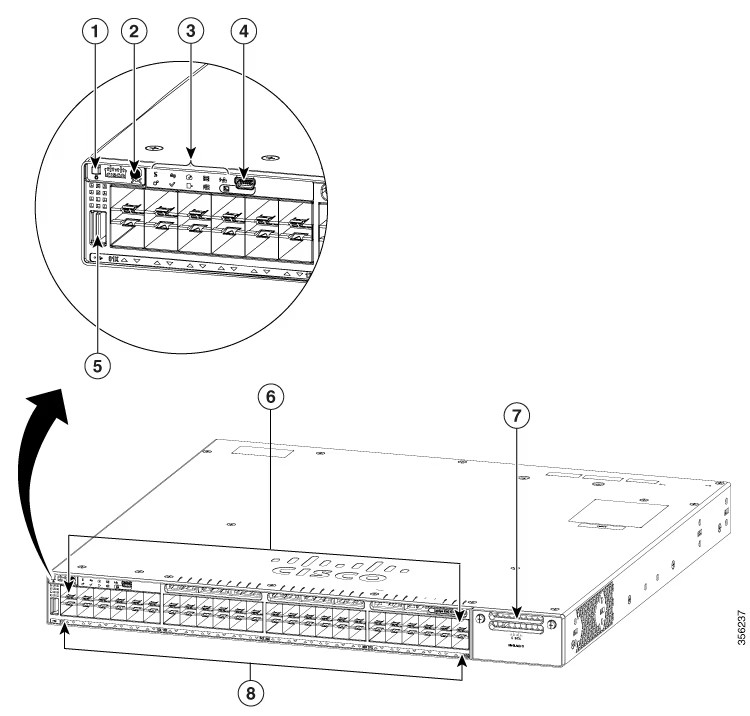






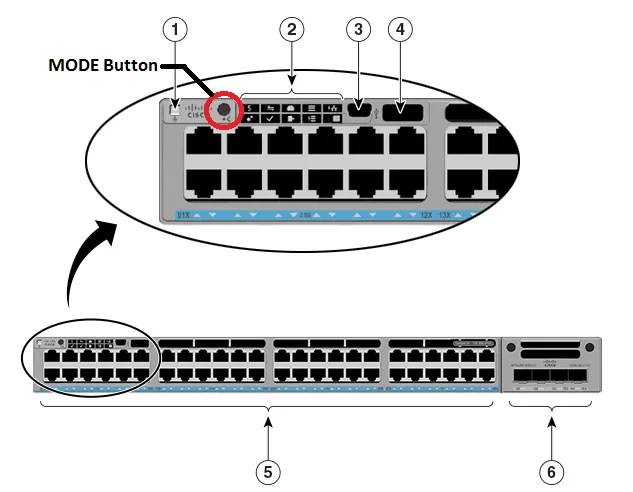




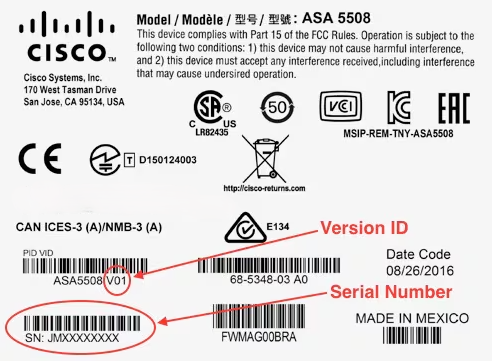




While robust passwords help you secure your valuable online accounts, hardware-based two-factor authentication takes that security to the next level.
Read nowThe US Commerce Department has released new rules designed to stop companies from selling hacking tools to China, Russia and other countries that may use them for nefarious purposes.
The new rules, which come into effect in 90 days and were pushed by the department's Bureau of Industry and Security (BIS), governs the "export, re-export, or transfer (in-country) of certain items that can be used for malicious cyber activities."
Companies would be barred from selling some technology to certain countries without a specific license from BIS.
US Secretary of Commerce Gina Raimondo said in a statement that the US is "committed to working with our multilateral partners to deter the spread of certain technologies that can be used for malicious activities that threaten cybersecurity and human rights."
"The Commerce Department's interim final rule imposing export controls on certain cybersecurity items is an appropriately tailored approach that protects America's national security against malicious cyber actors while ensuring legitimate cybersecurity activities," Raimondo said.
The rule additionally certifies a new License Exception Authorized Cybersecurity Exports (ACE) which the department is now looking for public comment on. The Commerce Department is looking for outside experts to let them know about how the rule will impact US companies and the wider cybersecurity community.
The department explained in a statement that the exception would "allow the export, re-export and transfer (in-country) of 'cybersecurity items' to most destinations while retaining a license requirement for exports to countries of national security or weapons of mass destruction concern."
Any country currently under a US arms embargo will need a license to receive certain technology.
"Furthermore, the License Exception ACE would impose an end-use restriction in circumstances where the exporter, re-exporter, or transferor knows or has reason to know at the time of export, re-export, or transfer (in-country), including a deemed export or re-export, that the 'cybersecurity item' will be used to affect the confidentiality, integrity or availability of information or information systems, without authorization by the owner, operator or administrator of the information system (including the information and processes within such systems)," the Commerce Department explained.
The department noted that the rule is in line with the Wassenaar Arrangement -- which voluntarily governs the export policies of 42 different countries around "military and dual-use technologies."
The US is one of the last countries that is part of the Wassenaar Arrangement to pass rules like this. China and Israel are not members of the Wassenaar Arrangement, but Russia is.
The rules come after an international outcry over a series of revelations about US experts and technology being used by repressive dictatorships. The US heavily fined three former NSA officials last month for providing the UAE with a slate of powerful hacking tools.
The three former US intelligence officials were part of Project Raven, an effort by the UAE to spy on human rights activists, politicians and dissidents opposed to the government. The three even hacked into US companies, creating two exploits that were used to break into smartphones.
Israeli officials continue to face backlash due to the tools provided by the NSO Group, a private company selling powerful spyware to dictatorships and cybercriminal groups.
The Washington Post was the first to report on the new rules from the Commerce Department, noting that the rules were specifically targeting companies that sell to Russia and China. The rule is complicated because of specific carve-outs meant to appease cybersecurity researchers who long complained about how the potential rules would make it difficult for them to share defensive information with others abroad.
One of the thorniest issues holding up the rule for years was the sale of penetration testing tools, which will be allowed without a license for certain countries but not allowed for others.
Jonathan Reiber, who previously served as the chief strategy officer for cyber policy in the Office of the US Secretary of Defense during the Obama administration, said it took a lengthy amount of time to put the rules in place because the government had to weigh the potential costs and benefits for any export control.
"It's not just time for deliberation within US government agencies and with Congress, but between the government, private industry and the research community. If you take a look at the rule itself and imagine the number of lawyers in various agencies that have to agree to the language before a rule can emerge publicly, you can begin to get a sense for why export control reform is a slow process," Reiber said.
"The Wassenaar Arrangement has been in place for decades, and as it matured over the last eleven years through the export control reform process, informing states' adoption of the controls within it, there were legitimate questions raised about how a potential export control could negatively impact the development and use of testing software intended to improve cybersecurity."
Reiber said this question was a hard one to solve because the export control reform process has to keep two principles in balance: to refrain from negatively impacting industry innovation while also controlling for potential negative scenarios that may arise from the proliferation of a potentially dangerous weapon or dual-use technology.
"Recent disclosures made crystal clear the risks that the proliferation of such software can pose, particularly for targeted individuals, dissident groups, and vulnerable populations that live at the mercy of oppressive regimes," Reiber added. "These events certainly may have accelerated the rules' development."
Chris Clements, vice president of solutions architecture at Cerberus Sentinel, said he does not foresee these rules having a significant impact on the overall offensive capabilities of many countries for several reasons.
Some of the biggest purveyors of such software are based outside the US, where the regulation may not affect them, he explained, adding that many of the most commonly used tools are open source in nature.
The open source nature of certain tools makes it unclear how these rules will impact their distribution.
"Even if common open-source hosting organizations such as GitHub or Gitlab were to enact GeoIP restrictions on the download of such designated intrusion software, it would seem trivial for a banned nation to simply VPN through a common VPN provider to bypass such restrictions," Clements said.
"Finally, it is often the case that actors in these jurisdictions make use of pirated versions of commercial tools, bypassing the need to acquire the software legitimately altogether."
 Горячие метки:
Технологии и оборудование
Безопасность и охрана
Горячие метки:
Технологии и оборудование
Безопасность и охрана